 Figure 1. Tool based design steps
Figure 1. Tool based design steps
Electrical and Computer Engineering Department
Faculty of Engineering, Campus No. 2
University of Tehran
14399, Tehran IRAN
Tel: +98-21-800-9215; Fax: +98-21-646-1024
Email: navabi@ece.ut.ac.ir
 Figure 1. Tool based design steps
Figure 1. Tool based design steps
 Figure 2. Initial processings on upper level descriptions
Figure 2. Initial processings on upper level descriptions
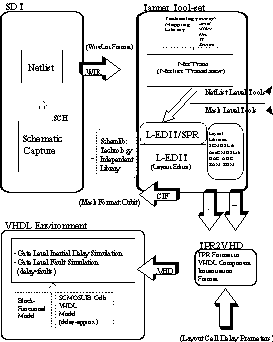 Figure 3. Extracting VHDL model from schematics
Figure 3. Extracting VHDL model from schematics
 Figure 4 . CSTP architecture
Figure 4 . CSTP architecture
|
--
|
|
--
|

7. CONCLUSIONS
We have presented methodologies for the design and verification of VLSI circuits. VHDL based tools are used in this process. Where needed programs for linking VHDL based tools and other VLSI tools have been developed. The paper has presented the use and implementation of a BIST architecture. This architecture not only is useful for final testing of the circuit, but it is also used for verifying design steps leading to the VLSI implementation of a relatively large design.